Design and analysis of data link impersonation attack for wired LAN application layer services | SpringerLink

Desktop Table Clock With Camera Mini Full HD 1080p Body Secret Small Micro Video Wifi IP Cam Night Vision Motion Sensor Secreta - Price history & Review | AliExpress Seller - Life





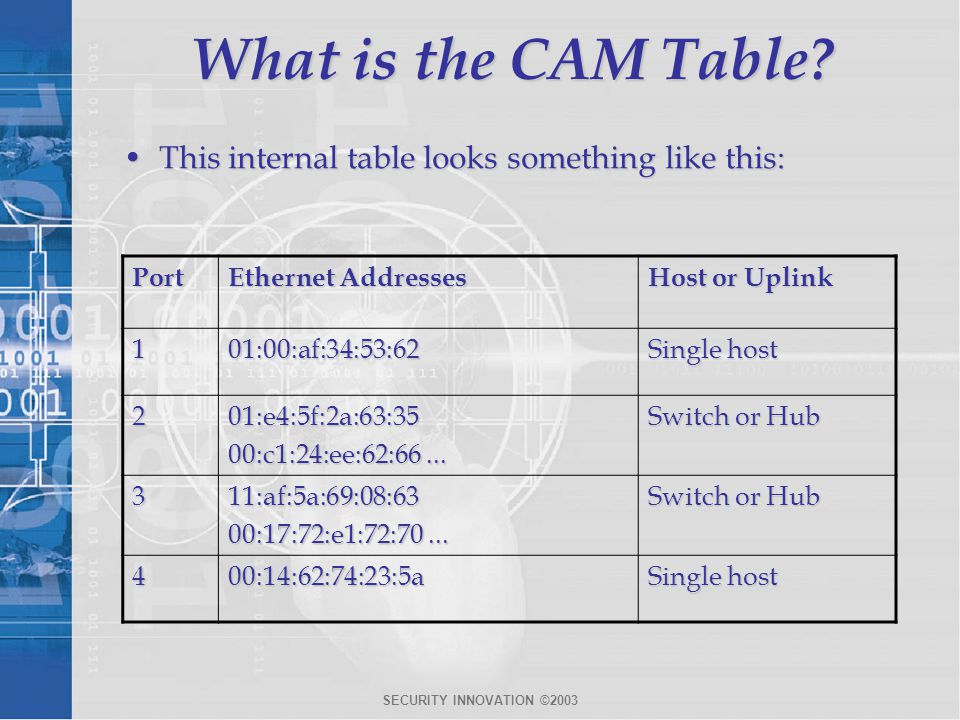




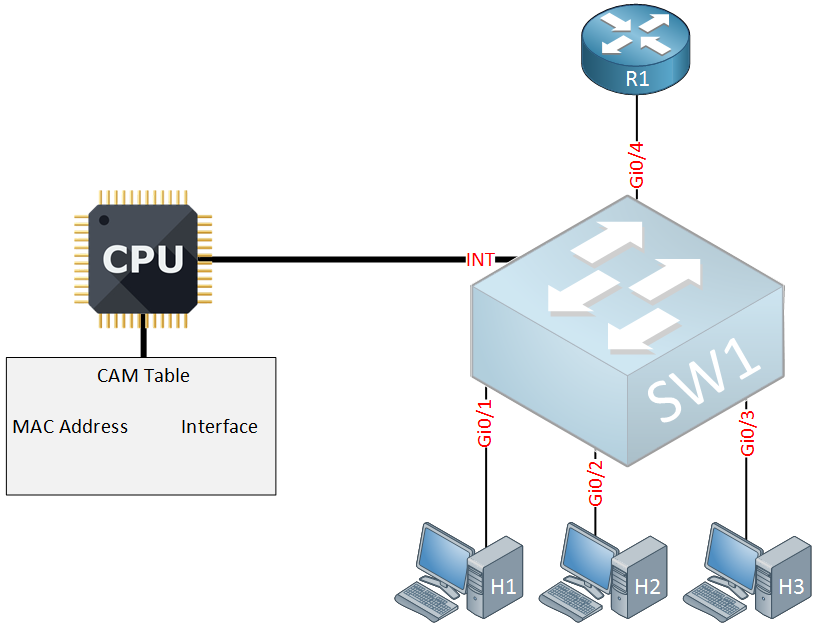
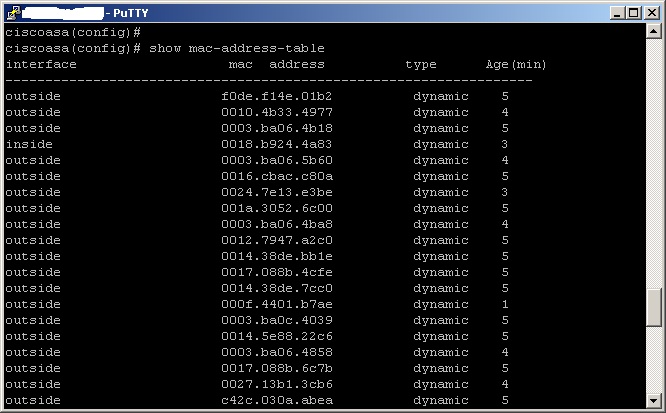




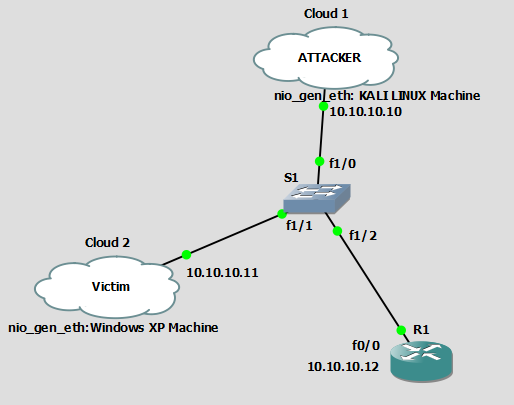

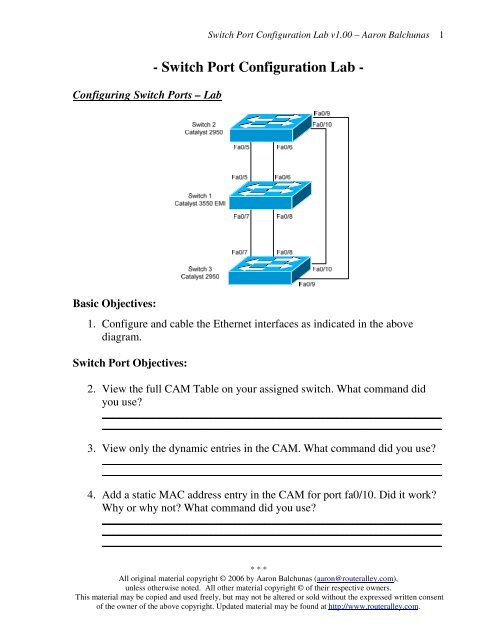
![How the switch uses the CAM tables - Python Penetration Testing Essentials [Book] How the switch uses the CAM tables - Python Penetration Testing Essentials [Book]](https://www.oreilly.com/api/v2/epubs/9781789138962/files/assets/4f76d848-e99f-42e0-b0e0-38b7d139b0df.png)