
Hacking: Computer Hacking, Security Testing, Penetration Testing, and Basic Security by Gary Hall, Erin Watson - Audiobook - Audible.com

Amazon.com: Hacking: Computer Hacking, Security Testing,Penetration Testing, and Basic Secur: 9781541289321: Hall, Gary, Watson, Erin: Libros

Hacking: Computer Hacking, Security Testing,Penetration Testing, and Basic Secur: Hall, Gary, Watson, Erin: 9781541289321: Amazon.com: Books

Hacking: Computer Hacking, Security Testing,Penetration Testing, and Basic Secur: Hall, Gary, Watson, Erin: 9781541289321: Amazon.com: Books
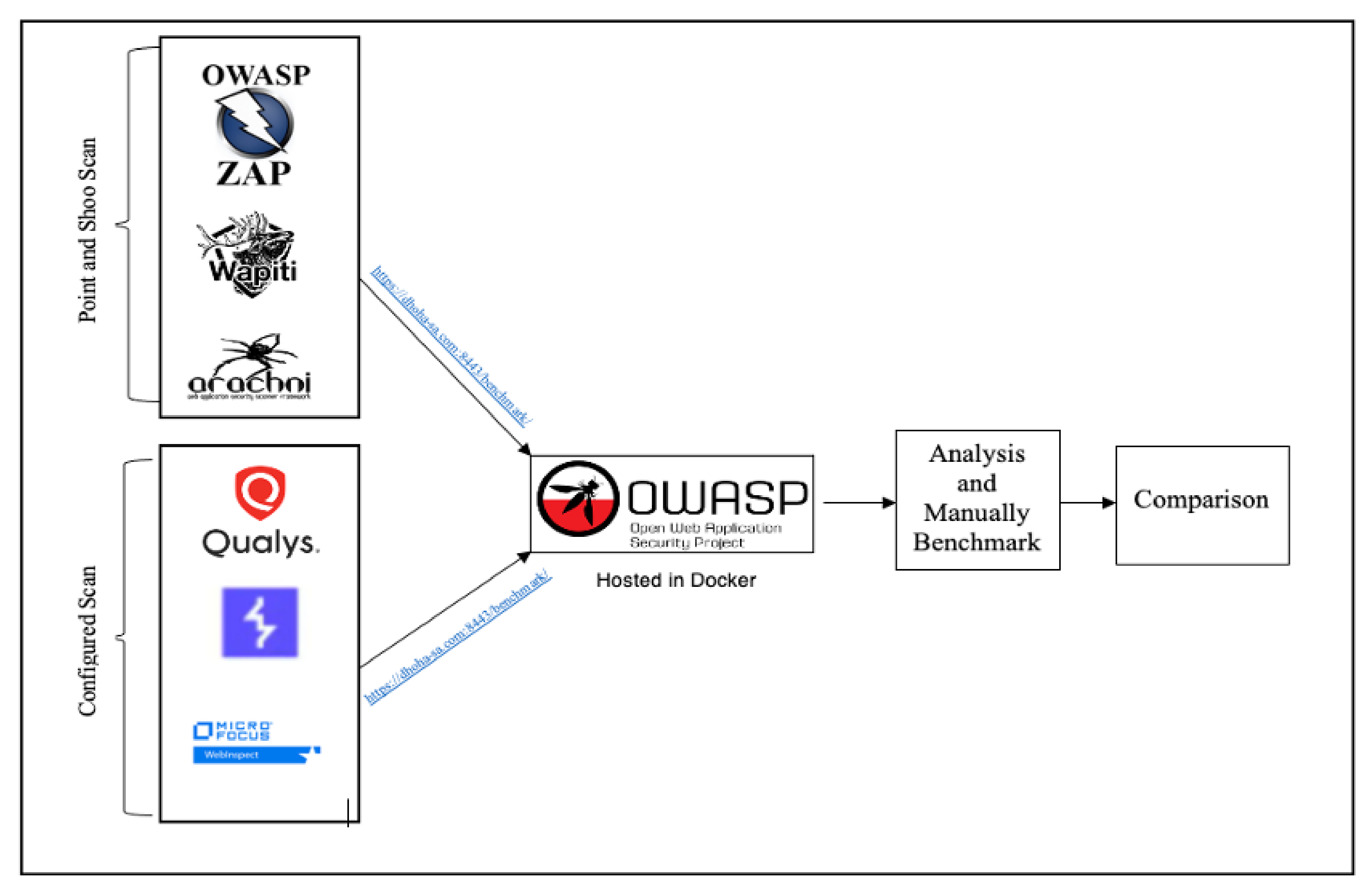
Electronics | Free Full-Text | An Empirical Comparison of Pen-Testing Tools for Detecting Web App Vulnerabilities

SOLUTION: How to hack computers how to hack computers hacking for beginners penetration testing hacking for dummies computer security computer hacking hacking techniques network scanning - Studypool
Hacking: Computer Hacking, Security Testing, Penetration Testing, and Basic Secur - Gary Hall, Erin Watson - 9781541289321 - Book | Kriso.ee

Hacking With Kali Linux : A Beginner's Guide with Detailed Practical Examples of Wireless Networks Hacking & Penetration Testing To Fully Understand Computer Cyber Security (Part 1) (Paperback) - Walmart.com







![PDF] Towards Side-Effects-free Database Penetration Testing | Semantic Scholar PDF] Towards Side-Effects-free Database Penetration Testing | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/bcf8bf3ad353eb4a887f0570727cf73e30ca1b83/3-Figure1-1.png)




